File/Firmware Oppo A31 CPH2015 Backup Normal-Link Google Drive
Ketua Teknisi HP (Official)
File/Firmware Oppo A31 CPH2015 Backup Normal-Link Google Drive.File kami backup menggunakan Ribak- Tool dalam kondisi smartphone normal jaya.manakala ini dibutuhkan untuk sesuatu,silahkan unduh filenya dengan gratis...
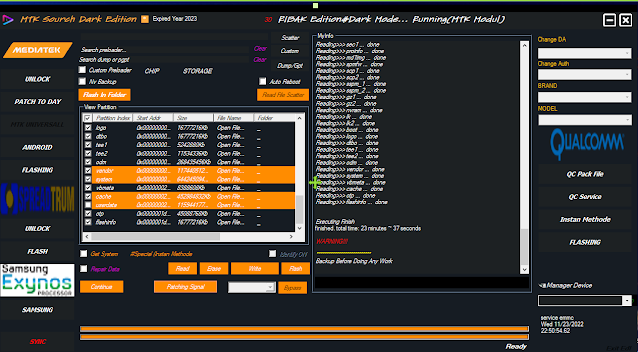 |
| MTK Sourch (RIBAK TOOL) |
Support Preloader:
EMIInfo{0x0}:150100444436384D42:0x15:Samsung:DD68MB:0x0:BGA (Discrete embedded):DRAM:MCP(eMMC+LPDR4X):3.00GB
EMIInfo{0x1}:13014E53304A394B39:0x13:Micron:S0J9K9:0x4e:BGA (Discrete embedded):DRAM:MCP(eMMC+LPDR4X):4.00GB
EMIInfo{0x2}:150100445636444D42:0x15:Samsung:DV6DMB:0x0:BGA (Discrete embedded):DRAM:MCP(eMMC+LPDR4X):4.00GB
EMIInfo{0x3}:13014E47314A395238:0x13:Micron:G1J9R8:0x4e:BGA (Discrete embedded):DRAM:MCP(eMMC+LPDR4X):4.00GB
EMIInfo{0x4}:90014A68423861503E:0x90:SkHynix:hB8aP>:0x4a:BGA (Discrete embedded):DRAM:MCP(eMMC+LPDR4X):3.00GB
EMIInfo{0x5}:90014A684339615033:0x90:SkHynix:hC9aP3:0x4a:BGA (Discrete embedded):DRAM:MCP(eMMC+LPDR4X):4.00GB
EMIInfo{0x6}:150100444836444142:0x15:Samsung:DH6DAB:0x0:BGA (Discrete embedded):DRAM:MCP(eMMC+LPDR4X):4.00GB
EMIInfo{0x7}:90014A684445615033:0x90:SkHynix:hDEaP3:0x4a:BGA (Discrete embedded):DRAM:MCP(eMMC+LPDR4X):6.00GB
EMIInfo{0x8}:150100335636434142:0x15:Samsung:3V6CAB:0x0:BGA (Discrete embedded):DRAM:MCP(eMMC+LPDR4X):6.00GB
EMIInfo{0x9}:13014E47314A395339:0x13:Micron:G1J9S9:0x4e:BGA (Discrete embedded):DRAM:MCP(eMMC+LPDR4X):4.00GB
Log Info:
Power Off ...
Brom Mode : Press Hold [Vol Up] + [Vol Down]
Please USB Connect...
Waiting for Brom Mode...
Status: Please Connect Mobile
... Device detected
CPU: MT6765/MT8768t(Helio P35/G35)
HW version: 0x0
WDT: 0x10007000
Uart: 0x11002000
Brom payload addr: 0x100a00
DA payload addr: 0x201000
CQ_DMA addr: 0x10212000
Var1: 0x25
Disabling Watchdog...
HW code: 0x766
Target config: 0xe5
SBC enabled: True
SLA enabled: False
DAA enabled: True
SWJTAG enabled: True
EPP_PARAM at 0x600 after EMMC_BOOT/SDMMC_BOOT: False
Root cert required: False
Mem read auth: True
Mem write auth: True
Cmd 0xC8 blocked: True
Get Target info
BROM mode detected.
HW subcode: 0x8a00
HW Ver: 0xca00
SW Ver: 0x0
ME_ID: 0A9071739589DA63CBDBB0EEDCCBAFCE
SOC_ID: B1D8ECF198BC8043625344474D97B14A67A33583369C79A6578DB9BF568680EA
Device detected
Uploading xflash stage 1 from MTK_AllInOne_DA_5.2152.bin
Successfully uploaded stage 1, jumping ..
Jumping to 0x200000
Jumping to 0x200000: ok.
Successfully received DA sync
DRAM config needed for : 13014e53304a394b
Sending emi data ...
DRAM setup passed.
Sending emi data succeeded.
Uploading stage 2...
Upload data was accepted. Jumping to stage 2...
Successfully uploaded stage 2
EMMC FWVer: 0x0
EMMC ID: S0J9K9
EMMC CID: 13014e53304a394b391017d6b7b71757
EMMC Boot1 Size: 0x400000
EMMC Boot2 Size: 0x400000
EMMC GP1 Size: 0x0
EMMC GP2 Size: 0x0
EMMC GP3 Size: 0x0
EMMC GP4 Size: 0x0
EMMC RPMB Size: 0x1000000
EMMC USER Size: 0x1d1f000000
HW-CODE: 0x766
HWSUB-CODE: 0x8A00
HW-VERSION: 0xCA00
SW-VERSION: 0x0
CHIP-EVOLUTION: 0x0
DA-VERSION: 1.0
Upload data was accepted. Jumping to stage 2...
DA Extensions successfully added
UserArea: 125074145280kb
Sectors: 244285440
MediaTek DA USB VCOM (Android) (COM25)
Get System Information...
BUILD ID : PPR1.180610.011
SECURITY PATCH : 2022-01-05
CPU ABI : arm64-v8a
CPU ABILIST : arm64-v8a,armeabi-v7a,armeabi
CPU ABILIST32 : armeabi-v7a,armeabi
CPU ABILIST64 : arm64-v8a
Manufacturer : OPPO
LOCALE : en-US
Build Description : full_oppo6765_19581-user 9 PPR1.180610.011 eng.root.20220107.130753 release-keys
BRAND : OPPO
MODEL : CPH2015
NAME : CPH2015
BUILD : OPPO/CPH2015/OP4C7D:9/PPR1.180610.011/1576852138:user/release-keys
Executing Finish
finished. total time: 0 minutes ~ 19 seconds
WARNING!!!
***************************
Backup Before Doing Any Work
Save To Folder: \\C:\Users\service emmc\Desktop\FILE BACKUPAN\Oppo A31
Power Off ...
Brom Mode : Press Hold [Vol Up] + [Vol Down]
Please USB Connect...
Waiting for Brom Mode...
Status: Please Connect Mobile
... Device detected
CPU: MT6765/MT8768t(Helio P35/G35)
HW version: 0x0
WDT: 0x10007000
Uart: 0x11002000
Brom payload addr: 0x100a00
DA payload addr: 0x201000
CQ_DMA addr: 0x10212000
Var1: 0x25
Disabling Watchdog...
HW code: 0x766
Target config: 0xe5
SBC enabled: True
SLA enabled: False
DAA enabled: True
SWJTAG enabled: True
EPP_PARAM at 0x600 after EMMC_BOOT/SDMMC_BOOT: False
Root cert required: False
Mem read auth: True
Mem write auth: True
Cmd 0xC8 blocked: True
Get Target info
BROM mode detected.
HW subcode: 0x8a00
HW Ver: 0xca00
SW Ver: 0x0
ME_ID: 0A9071739589DA63CBDBB0EEDCCBAFCE
SOC_ID: B1D8ECF198BC8043625344474D97B14A67A33583369C79A6578DB9BF568680EA
Device detected
Uploading xflash stage 1 from MTK_AllInOne_DA_5.2152.bin
Successfully uploaded stage 1, jumping ..
Jumping to 0x200000
Jumping to 0x200000: ok.
Successfully received DA sync
DRAM config needed for : 13014e53304a394b
Sending emi data ...
DRAM setup passed.
Sending emi data succeeded.
Uploading stage 2...
Upload data was accepted. Jumping to stage 2...
Successfully uploaded stage 2
EMMC FWVer: 0x0
EMMC ID: S0J9K9
EMMC CID: 13014e53304a394b391017d6b7b71757
EMMC Boot1 Size: 0x400000
EMMC Boot2 Size: 0x400000
EMMC GP1 Size: 0x0
EMMC GP2 Size: 0x0
EMMC GP3 Size: 0x0
EMMC GP4 Size: 0x0
EMMC RPMB Size: 0x1000000
EMMC USER Size: 0x1d1f000000
HW-CODE: 0x766
HWSUB-CODE: 0x8A00
HW-VERSION: 0xCA00
SW-VERSION: 0x0
CHIP-EVOLUTION: 0x0
DA-VERSION: 1.0
Upload data was accepted. Jumping to stage 2...
DA Extensions successfully added
Reading>>> boot_para ... done
Reading>>> recovery ... done
Reading>>> para ... done
Reading>>> opporeserve1 ... done
Reading>>> opporeserve2 ... done
Reading>>> opporeserve3 ... done
Reading>>> oppo_custom ... done
Reading>>> expdb ... done
Reading>>> frp ... done
Reading>>> nvcfg ... done
Reading>>> nvdata ... done
Reading>>> metadata ... done
Reading>>> protect1 ... done
Reading>>> protect2 ... done
Reading>>> seccfg ... done
Reading>>> persist ... done
Reading>>> sec1 ... done
Reading>>> proinfo ... done
Reading>>> md1img ... done
Reading>>> spmfw ... done
Reading>>> scp1 ... done
Reading>>> scp2 ... done
Reading>>> sspm_1 ... done
Reading>>> sspm_2 ... done
Reading>>> gz1 ... done
Reading>>> gz2 ... done
Reading>>> nvram ... done
Reading>>> lk ... done
Reading>>> lk2 ... done
Reading>>> boot ... done
Reading>>> logo ... done
Reading>>> dtbo ... done
Reading>>> tee1 ... done
Reading>>> tee2 ... done
Reading>>> odm ... done
Reading>>> vendor ... done
Reading>>> system ... done
Reading>>> vbmeta ... done
Reading>>> cache ... done
Reading>>> otp ... done
Reading>>> flashinfo ... done
Executing Finish
Oppo_A31_ CPH2015.Selamat mencoba dan semoga sukses.Download Juga Firmware Oppo A15 Cloning/Refurbish











